Twidget supports Bearer Authentication to ensure secure access to your endpoints. You can specify which endpoints should be secured or open. Once secured, an endpoint can only be accessed using a valid Bearer Token, which is generated via our API. Additionally, we provide functionality to generate authentication endpoints to handle user sign-up and token generation.
Bearer Authentication is a security mechanism for ensuring that only authorized users can access certain resources. It is commonly used in API security protocols and involves the use of Bearer Tokens.
-
A Bearer Token is a type of access token that is included in the HTTP headers of a request. This token is used to authenticate requests to protected resources:
Format: Typically, a Bearer Token is a string that is generated by the authentication server.
Usage: The client must include this token in the Authorization header of their HTTP requests to access secured endpoints.
Example:
Authorization: Bearer <token>
Bearer token in the Authorization header of a request
User Sign-Up/Login: Users sign up or log in via an authentication endpoint. During this process, they provide credentials which are validated by the server.
Token Generation: Upon successful authentication, a Bearer Token is generated by the server and returned to the user.
Access Secured Endpoints: The user includes the Bearer Token in the HTTP headers when making requests to secured endpoints. The server verifies the token before granting access to the resource.
Twidget allows you to specify which endpoints should be secured. You can do this via a straightforward configuration:
Unsecured Endpoints: These endpoints are open to all users and do not require a token for access.
Secured Endpoints: These endpoints require a valid Bearer Token. Without the token, access to the resource is denied.
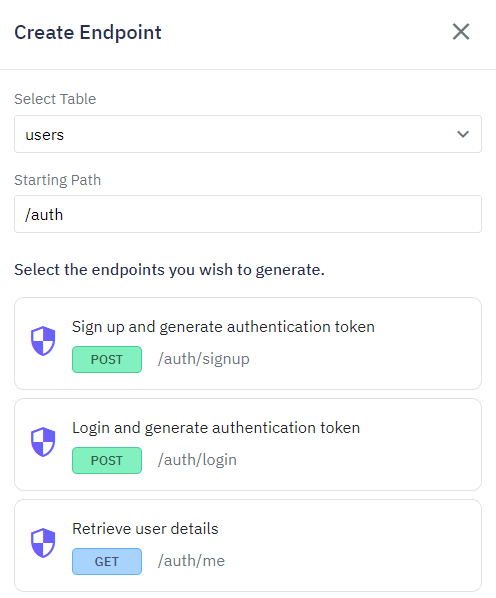
Twidget enables you to easily generate the necessary authentication endpoints for user sign-up, login, and token generation. These endpoints include:
Sign-Up Endpoint: Allows new users to register and receive a Bearer Token upon successful registration.
Login Endpoint: Allows existing users to log in and receive a Bearer Token upon successful authentication.
Token Refresh Endpoint: Optionally, users can refresh expired or soon-to-expire tokens.
User Sign-Up: The user sends a POST request to the sign-up endpoint with their credentials.
User Login: The user sends a POST request to the login endpoint with their credentials.
Token Response: Upon successful authentication, the user receives a Bearer Token.
Access Resource: The user includes the Bearer Token in the Authorization header when requesting a secured resource.
Bearer Authentication is a robust security mechanism to protect your API endpoints. By leveraging the features provided by Twidget, you can easily implement and manage authentication, ensuring that only authorized users have access to your secured resources.
API Settings
The API settings in Twidget enable you to customize your APIs to fit your requirements. Here’s how you can do it: Configure. 1. Navigate to the API page. 2. Click on the Settings button located at the top-right corner. This will open a sidebar where you can configure various settings for your API. A...
Generate CRUD Endpoints
What are CRUD Endpoints?. CRUD stands for Create, Read, Update, Delete. These are the basic operations required to manage data in a database. Each operation corresponds to a specific HTTP method: - Create: Adds new data (HTTP POST) - Read: Retrieves data (HTTP GET) - Update: Modifies existing data (...
Endpoint Basics
An endpoint refers to a specific URL (Uniform Resource Locator) that a client can access to interact with the API and perform various operations. Endpoints act as gateways that allow clients (such as web or mobile applications) to communicate with the server hosting the API and perform actions like ...
Creating Authentication Endpoints
Follow these steps to create authentication endpoints in Twidget: Step-by-Step Guide. 1. Navigate to API Tab: - Go to the `API` tab in your Twidget dashboard. 2. Create New Endpoints: - Click on the `Create Endpoints` button located at the top right corner. 3. Select Authentication: - In the newly o...
What is an API
An API (Application Programming Interface) is a set of rules and protocols that allows different software applications to communicate and interact with each other. It defines the methods and data formats that applications can use to request and exchange information, services, or functionalities from...